Global Crackdown on Crypto Ransomware Hosts
In a major international effort to curb the damaging impact of crypto ransomware, authorities in the United States, the United Kingdom, and Australia have imposed sanctions on a Russia-based bulletproof hosting provider called Zservers. This crackdown comes after Zservers was accused of supplying hosting services to the notorious LockBit ransomware gang, which has caused billions of dollars in damage to individuals, businesses, and critical infrastructure worldwide.
The sanctions target Zservers directly, as well as its UK-based subsidiary, XHOST Internet Solutions LP, freezing assets and imposing travel bans on six individuals allegedly connected to the operation. The sanctions were announced on February 11, 2024, by the US Treasury’s Office of Foreign Assets Control (OFAC) and the UK’s Foreign Office.
How Zservers Enabled Cybercrime
Zservers is a “bulletproof hosting” provider, a term used to describe services that shield cybercriminals by masking their activities, identities, and locations online. These services allow hackers to operate more freely and securely, often bypassing law enforcement and security efforts. According to Bradley Smith, the acting under-secretary for terrorism and financial intelligence at the US Treasury, cybercriminals heavily rely on companies like Zservers to conduct large-scale attacks on critical infrastructure both in the US and internationally.
In February 2024, a joint operation by authorities from 10 countries, including the US, the UK, and Australia, targeted the LockBit ransomware group, which is accused of being behind the cyberattacks that have caused massive financial losses. LockBit’s operations are said to have been responsible for some of the most high-profile cyberattacks in recent years, including hacks on Australia’s Medibank and the Industrial and Commercial Bank of China US branch. The ransomware group is infamous for encrypting victims’ data and demanding cryptocurrency payments in exchange for the decryption key.
Sanctions Target Key Individuals Behind Zservers
Among those sanctioned are two Russian nationals: Alexander Igorevich Mishin and Aleksandr Sergeyevich Bolshakov, who are alleged to be key figures behind Zservers’ operations. Mishin and Bolshakov are accused of facilitating LockBit’s ransomware attacks by coordinating crypto transactions and supporting the gang’s activities.
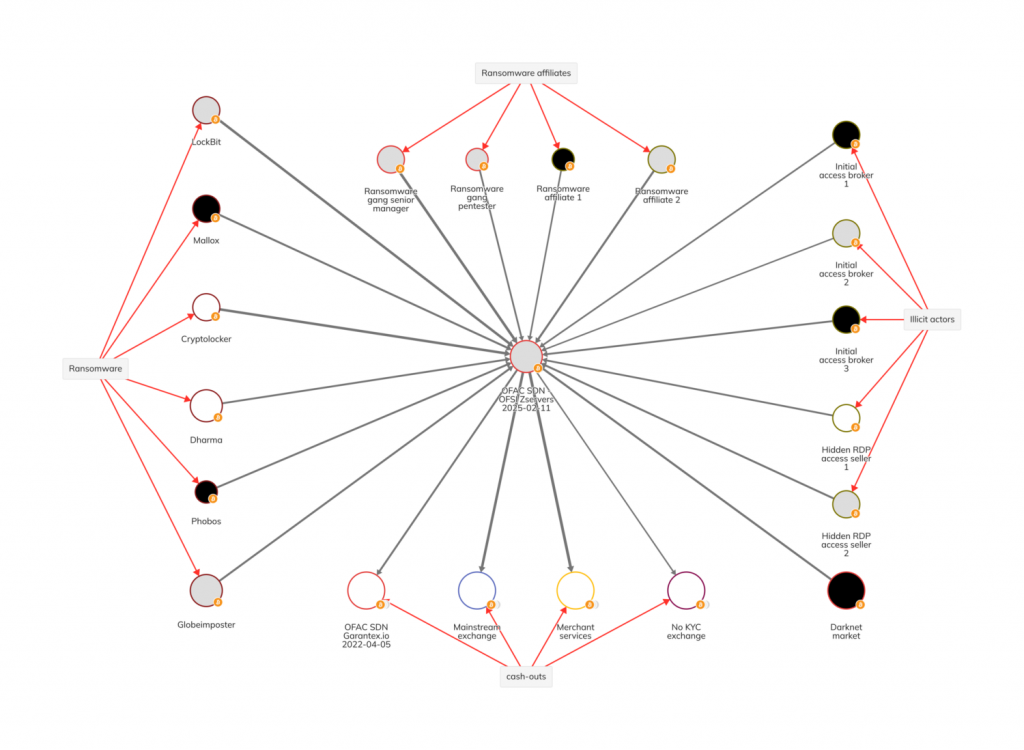
In addition to the individuals, OFAC has added crypto addresses linked to Zservers to its Specially Designated Nationals (SDN) list, which places them under special sanctions. According to blockchain analytics firm Chainalysis, one of the crypto addresses tied to Mishin and three others associated with Zservers are now blacklisted. This move follows a similar crackdown in August 2022 when OFAC sanctioned Tornado Cash smart contracts for allegedly laundering over $7 billion in cryptocurrency.
Tracking Zservers’ Ransomware Revenue
Chainalysis has also provided insight into Zservers’ financial activities, revealing that the hosting provider facilitated significant funds flows from ransomware groups beyond LockBit. Zservers was reportedly linked to several ransomware affiliates, cashing out funds through Garantex, a Russian-based exchange that has been sanctioned for lack of proper anti-money laundering protocols.
Further analysis of Zservers’ on-chain activities shows over $5.2 million in funds moved through its infrastructure, much of it connected to high-risk and illicit activities. Zservers’ operations were reportedly spread across multiple countries, including the US, Russia, Bulgaria, the Netherlands, and Finland, with a range of servers used to support ransomware activities and other criminal enterprises.
LockBit: A Ransomware Group with Massive Reach
LockBit has been a thorn in the side of international cybersecurity efforts since it first emerged in 2019. Known for its sophisticated and highly effective ransomware campaigns, LockBit is estimated to have extorted up to $1 billion over the course of more than 7,000 cyberattacks between June 2022 and February 2024. The group has become notorious for not just locking files but also threatening to leak sensitive data if ransom demands are not met, creating a sense of urgency among victims to comply.
The group has evolved its tactics over time, using advanced encryption methods and engaging in double extortion, where they not only demand payment to decrypt files but also to prevent the release of stolen data. This combination of high stakes and technological prowess has made LockBit one of the most damaging ransomware gangs to date.
The Bigger Picture: International Cooperation Against Ransomware
The sanctions against Zservers and the ongoing efforts to dismantle LockBit underscore the increasing international cooperation to combat ransomware and cybercrime. With ransomware attacks becoming more frequent and sophisticated, governments around the world are stepping up their efforts to disrupt the operations of these criminal networks.
The joint action taken by 10 countries is part of a broader initiative to protect critical infrastructure from digital threats, especially those that exploit cryptocurrency for illicit gains. As cybercrime continues to evolve, it’s clear that the fight against ransomware will require a coordinated, global effort.
For Zservers, this latest round of sanctions is likely to have significant consequences, as it further isolates the company and its affiliates from the global financial system. The hope is that by disrupting the infrastructure that powers ransomware attacks, authorities can reduce the impact of these increasingly common and damaging crimes.
Looking Ahead: A Continued Global Effort to Tackle Ransomware
As ransomware groups like LockBit continue to evolve, the international community will need to remain vigilant and proactive in their efforts to curb cybercrime. Sanctions like those against Zservers are just one piece of the puzzle, but they are an essential part of the global strategy to protect businesses, governments, and individuals from the growing threat of ransomware.
With authorities working together across borders and leveraging tools like blockchain analytics, the fight against ransomware is becoming a more coordinated and effective effort—but it’s clear that much work remains to be done.



